
Only five out of 104 NSW agencies have implemented mandatory cybersecurity controls at the expected baseline of the Government’s Cyber Security Policy (CSP), with the Auditor-General’s latest cyber report flagging “poor levels of cyber security maturity” within state agencies.
The belatedly released report, conducted in June and since modified to anonymise still cyber-vulnerable agencies, found not only poor implementation of mandated security controls but also a significant over-estimation of agencies’ cybersecurity capability.
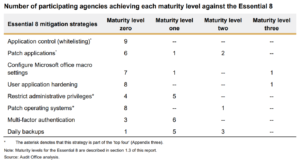
An in-depth audit of nine NSW agencies revealed that eight of these had failed to implement any of the Essential Eight (E8) cybersecurity controls to an accepted baseline standard – that is, a maturity level of Three for each mitigation strategy.
Moreover, the audit found that not one agency had met a Level One maturity (at the time, the minimum benchmark) for at least three of the Essential Eight controls.
The E8, established by the Federal Government’s Australian Cyber Security Centre (ACSC), sets out mitigation strategies to shield organisations from cyber threats. The controls are considered the ACSC’s highest priority mitigation strategies and the most effective measures to defend against cyber-attacks.
Organisations can rate their overall security posture against the E8’s benchmark standards for, for instance, delivery of regular back-ups and patching, the use of multi-factor authentication and administrator privilege setting, among others.
Level Three – while the highest of the E8’s four maturity levels (from Level Zero to Level Three) is also considered a baseline for Australian government agencies – focuses on resisting higher-level adversaries “who are more adaptive and much less reliant on public tools and techniques”.
“These adversaries are able to exploit the opportunities provided by weaknesses in their target’s cyber security posture, such as the existence of older software or inadequate logging and monitoring,” the ACSC states.
Maturity Level Zero, reinstated by the ACSC in July this year as the lowest level of maturity under the E8 model, “signifies… weaknesses in an organisation’s overall cyber security posture”.
“When exploited, these weaknesses could facilitate the compromise of the confidentiality of their data, or the integrity or availability of their systems and data,” the ACSC notes.
“[As] a baseline, organisations should aim to reach to reach maturity Level Three for each mitigation strategy,” the ACSC notes.
The NSW auditor found that not one of the participating agencies in the survey had implemented all Essential 8 controls to at least Level One. (However, the auditor noted that, having been removed from the E8 in 2019 and then reinstated in June 2021, a Level Zero assessment was not part of the framework at the time the audit was conducted).
Under version 4.0 of the NSW Government’s Cyber Security Policy (CSP), all NSW Government departments and public service agencies are obligated to implement the Essential Eight.
The Department of Customer Services (DCS) which oversees Cyber Security NSW (the agency tasked with delineating the CSP), has only recommended, but not mandated the CSP for state-owned corporations, local councils and universities.
The Federal Government in July this year also flagged its intention to mandate the E8 for all 98 non-corporate Commonwealth entities.
The NSW auditor stressed that “poor levels of maturity in implementing the Essential Eight over the last couple of years is an area of significant concern” for the Government.
It added that “better leadership and resourcing” will be needed to “prioritise the required significant improvement in agency cyber security measures”.
What is more, the auditor also revealed inconsistencies in the implementation of the NSW Government’s own CSP provisions, which are based on a five-point scale.
It found that “agencies can decide not to implement requirements of the CSP, or they can decide to implement them only in an informal or ad-hoc manner”.
So far, only five out of the 104 agencies self-assessed that they had implemented all of the mandatory requirements at level three or above (against the five-point scale of the CSP). Agencies are required to self-assess their own cyber maturity once a year – against both the CSP and E8.
Perhaps more strikingly, it found that agencies “tended to over-assess their cybersecurity maturity, with all nine participating agencies unable to support some of their self-assessments of compliance with one or more mandatory criteria.”
For instance, it found two agencies reported they had an approved cyber security plan. However, it was later found by the auditor that neither agency had any such plan in place.
The report added: “Optimistic assessment of the current state of cyber resilience undermines effective decision making and risk management in responding to cyber risks.”
For agencies to comply with at least “some elements of the government’s policy”, the auditor warned that investments in technical uplift and other necessary uplift measures “may take time to implement”.
Nevertheless, the report added, these measures may not necessarily require costly investment in new technologies.
“They simply require leadership and management commitment to improve cyber literacy and culture. And they require accountability and transparency.
“Transparent reporting of performance is a key means to improve performance.”
The nine specific agencies of concern were “anonymised” in the report (with the auditor acknowledging their increased exposure as “vulnerabilities [had] yet to be remedied”). Among the nine agencies included the DP&C, Customer Service, Education, Health, Transport departments and the Treasury.
Audited agencies requested that findings from the audit not be reported to NSW Parliament, despite being more than 12 months old, believing this could risk exposing their weaknesses to threat actors.
NSW Auditor-General Margaret Crawford in her foreword to the report said she had “reluctantly agreed to modify my report to anonymise agencies and their specific failings because the vulnerabilities identified have not yet been remedied”.
“Time, leadership and prioritised action should have been sufficient for agencies to improve their cyber safeguards.”
“I am of the view that transparency and accountability to the Parliament is part of the solution, not the problem,” Crawford said.





